cybersecurity crossing®
by chapsvision
Protect your sensitive information systems.
An integrated security device, CrossinG® by ChapsVision allows you to isolate a critical network, filter and clean up content exchanged with an open network.
With CrossinG® by ChapsVision, you can easily monitor and decide what goes in and out of your network.
Enable controlled and secure exchanges
Between open and
sensitive networks
Isolate your critical resources
And protect them from network attacks
Facilitate regulatory compliance
And seamless integration into the business environment
Facilitate regulatory compliance
And cybersecurity best practices
Crossing® by chapsvision
CrossinG® by ChapsVision allows you to control flows, guarantee confidentiality and integrity of exchanges between two information systems, while maintaining a strict separation between networks of different sensitivities.
The strong partitioning and content analysis prevent the risk of propagation of an attack from one network to another, the injection of malicious content and data leakage.
Delivered as an integrated, multi-functional appliance, CrossinG® by ChapsVision provides transfer performance, ease of operation, and compliance assurance.
CrossinG® by ChapsVision provides effective protection for critical networks that cannot be satisfied with a firewall.
AN INTEGRATED SECURITY DEVICE

CrossinG® by ChapsVision isolates a critical network, filters and depollutes content exchanged with an open network, and:
- Verify the integrity of incoming files and protect the network from malicious content
- Check the integrity of incoming files and protect the network from malicious content
- Filter outgoing files and reduce the risk of data leakage
- Block cascading contamination by breaking the network
- Block any attempt to remotely take control of a system, machine or sensor
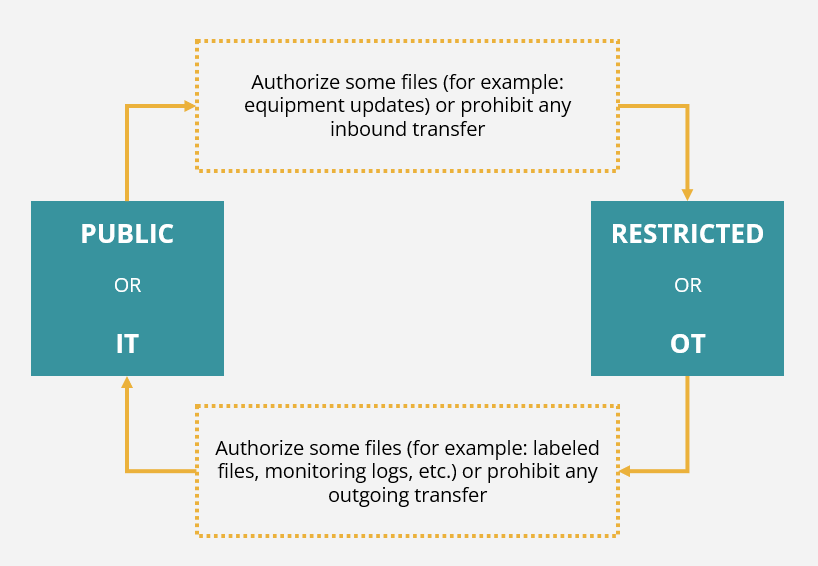
EASILY MONITOR AND DECIDE WHAT GOES IN AND OUT OF YOUR NETWORKS
Configurable in single-(diode) or bi-directional modes, CrossinG® by ChapsVision allows you to define a specific security policy depending on the direction of the transfer. For example, it is possible to allow only certain types of files to enter or leave the network, or even to prohibit all incoming and outgoing files at any time.
CrossinG® by ChapsVision also ensures the traceability of all transfers and cleanup processes.
SECURITY FEATURES

- Network break isolation
- 4 physically isolated network interfaces
- Unidirectional flow (diode)
- Two isolated unidirectional transfer channels, A to B and B to A
- Anti-virus, anti-malware checks
- Signature and label checking
- High transfer performance
- Volume processing capability
- Clustering
- Centralized administration console for input and output, administration and monitoring.
- Sender authentication and traceability
- Drag and drop transfer control
- Privilege Access Management (PAM) compatibility
- CDR – Content Disarm & Reconstruction
- Integrity and format checking (.exe, hidden workloads, malformed files, etc.)
- Whitelisting of files (MIME + extension)
- Neutralisation by conversion of text, PDF, Office and image files
- Automatic document watermarking
The CrossinG® by ChapsVision gateway complies with the rules relating to the partitioning and filtering to which the OIV are subjected within the framework of the Military Programming Law (LPM). It also enables compliance with the NIS directive for OSEs, the IEC 62443 standard and the II901.
MULTIPLE USE CASES
ENERGY ENVIRONMENT AND OTHER INDUSTRIES
CrossinG® by ChapsVision protects sensor feedback from production equipment to the control centre and supervisory authority.
SECURITY OPERATION CENTre
CrossinG® by ChapsVision protects the exchange areas between the external SOC and the corporate network.
MEDIA
AUDIOVISUAL
CrossinG® by ChapsVision protects the import of digital content into the production/broadcast control room.
PRODUCTION
IT
CrossinG® by ChapsVision protects the import of updates and the export of logs to/from the AIS (administration network).